The Role of Unified Endpoint Management in Enhancing Enterprise Security
Introduction
In today’s rapidly evolving digital landscape, enterprises face a growing number of security challenges. The proliferation of mobile devices, remote work environments, and the Internet of Things (IoT) has expanded the attack surface, making traditional security solutions inadequate. Unified Endpoint Management, or UEM, is useful in this situation. Desktops, laptops, smartphones, tablets, and Internet of Things (IoT) devices can all be managed and secured using UEM, a comprehensive solution, from a single platform. By centralizing management, UEM not only enhances device security but also improves operational efficiency and compliance with regulatory requirements.
Definition
Unified Endpoint Management (UEM) is a comprehensive platform that allows organizations to manage, monitor, and secure a variety of devices such as desktops, laptops, smartphones, tablets, and IoT devices from a single, centralized interface. UEM integrates functionalities like mobile device management (MDM), application management, security policy enforcement, and remote monitoring to ensure consistent control across all endpoints. By providing a unified approach, UEM simplifies device management, enhances security, and helps ensure compliance with organizational and regulatory standards, making it an essential tool in today’s multi-device enterprise environments.
What is Unified Endpoint Management (UEM)?
Unified Endpoint Management is an all-encompassing solution that enables IT teams to monitor, manage, and secure endpoints (devices) from a centralized platform. UEM solutions typically provide:
- Device Management: Mobile devices (smartphones, tablets), desktops, laptops, and even Internet of Things devices are all managed via UEM systems.
- Security Enforcement: UEM helps enforce security policies across all devices, ensuring compliance with organizational standards.
- App and Data Management: UEM offers capabilities for managing the distribution and usage of applications and data on managed devices.
- Remote Monitoring and Troubleshooting: UEM platforms provide real-time monitoring and the ability to troubleshoot devices remotely.
- Compliance Management: UEM solutions help businesses ensure that their devices comply with internal policies and external regulations (GDPR, HIPAA, etc.).
By consolidating all endpoint management functions into a single solution, UEM reduces the complexity of managing an increasingly diverse array of devices, making it easier to maintain a secure and compliant environment.
The Growing Need for UEM in Enterprises
Endpoint security is becoming more and more important in the modern enterprise. As businesses adopt more flexible work environments, such as remote work and bring-your-own-device (BYOD) policies, managing and securing the growing number of endpoints has become increasingly challenging. Each new device connected to the corporate network represents a potential vulnerability that could be exploited by cyber attackers.
Here are some key reasons why Unified Endpoint Management is essential for enterprise security:
- Proliferation of Devices: Enterprises today use a diverse range of devices, including desktops, laptops, mobile devices, and IoT devices. Managing and securing each device individually is inefficient and prone to errors. UEM centralizes the management of these devices, ensuring consistent security policies across the board.
- BYOD and Remote Work: The complexity of addressing security risks has increased with the advent of remote work and the BYOD trend. Employees use personal devices to access corporate networks, which increases the potential for data breaches and security vulnerabilities. UEM helps manage and secure these personal devices as effectively as corporate-owned devices.
- Increasing Cyber Threats: Cyberattacks are becoming more sophisticated, targeting not only network infrastructures but also endpoint devices. Phishing, ransomware, and malware attacks often originate from compromised endpoints. UEM provides robust security features like encryption, multi-factor authentication, and threat detection to protect devices from these threats.
- Compliance Requirements: Many industries have strict compliance regulations governing data protection and privacy. UEM solutions help organizations meet these requirements by enforcing security policies, controlling access to sensitive data, and providing auditing and reporting features.
Key Components of UEM for Enhancing Security
Unified Endpoint Management platforms offer a wide range of features that help businesses enhance security across their network of devices. Some of the key components include:
- Centralized Policy Enforcement: UEM solutions allow IT teams to enforce security policies across all endpoints, regardless of their location or type. This ensures that devices are always compliant with security standards, whether they are within the corporate network or used remotely.
- Mobile Device Management (MDM): A core feature of UEM, MDM helps manage and secure mobile devices, including smartphones and tablets. It allows IT teams to enforce password policies, encrypt data, and remotely wipe devices if they are lost or stolen.
- Endpoint Detection and Response (EDR): EDR is a critical feature of UEM that enables real-time monitoring of endpoint activities to detect and respond to security incidents. It helps identify unusual behavior, such as unauthorized access attempts or suspicious file transfers, and triggers alerts for IT teams to take action.
- Application Management: UEM platforms enable IT teams to control which applications can be installed and used on managed devices. This helps prevent the installation of malicious or unauthorized applications that could compromise security.
- Patch Management: UEM ensures that all devices are updated with the latest security patches and software updates. As a result, attackers are less likely to take advantage of weaknesses.
- Data Encryption and Remote Wipe: UEM platforms provide encryption for data stored on endpoints and allow IT teams to remotely wipe data from devices to make sure that private information does not get up in the wrong hands in the event that they are misplaced or stolen.
- Identity and Access Management (IAM): By integrating IAM capabilities, UEM ensures that only authorized users can access enterprise resources. Features such as single sign-on (SSO), multi-factor authentication (MFA), and role-based access controls enhance security by preventing unauthorized access to sensitive data and systems.
Benefits of Unified Endpoint Management for Enterprise Security
The adoption of UEM offers several key benefits to enterprises seeking to improve their security posture. Here are some of the main advantages:
1. Enhanced Visibility and Control
UEM platforms provide IT teams with full visibility and control over all endpoint devices in the network. With a unified view of device activities, configurations, and security status, IT administrators can quickly identify potential vulnerabilities and take corrective actions. This centralized control also helps ensure that security policies are consistently enforced across all devices.
2. Improved Security Compliance
With UEM, enterprises can easily meet industry-specific regulatory requirements such as GDPR, HIPAA, and PCI DSS. UEM platforms provide auditing, reporting, and monitoring tools that make it easier to demonstrate compliance and identify any gaps in security practices. Additionally, automated enforcement of policies ensures that devices remain compliant at all times.
3. Reduced Risk of Data Breaches
By securing all endpoints through encryption, threat detection, and access controls, UEM significantly reduces the risk of data breaches. Even if a device is lost or compromised, UEM’s remote wipe and lockdown features ensure that sensitive data remains protected.
4. Increased Operational Efficiency
A single platform for device configuration, monitoring, and troubleshooting is provided by UEM, which streamlines the management of numerous devices. This reduces the time and effort needed to maintain security across different device types, allowing IT teams to focus on more strategic initiatives. Automation of tasks such as software updates and patch management also reduces the likelihood of human error.
5. Scalability and Flexibility
As enterprises grow and adopt more devices, UEM platforms can easily scale to manage the increased number of endpoints. UEM solutions are designed to be flexible, allowing businesses to manage a wide variety of devices, including IoT devices, from a single platform. This adaptability ensures that the enterprise remains secure, even as its technology ecosystem evolves.
How UEM Helps Combat Evolving Cyber Threats
As cyber threats continue to evolve, UEM plays a vital role in keeping enterprises secure by offering a proactive approach to endpoint management and security. Key ways in which UEM helps combat modern cyber threats include:
- Real-Time Threat Detection: UEM platforms provide real-time monitoring of endpoints, enabling businesses to detect threats early and respond quickly before they cause significant damage.
- Automation of Security Tasks: UEM automates critical security tasks such as patch management and software updates, reducing the risk of vulnerabilities being exploited by attackers.
- Zero Trust Security Models: Many UEM solutions support the implementation of zero-trust security models, which verify the identity of users and devices before granting access to resources. This helps prevent unauthorized access to sensitive data and systems.
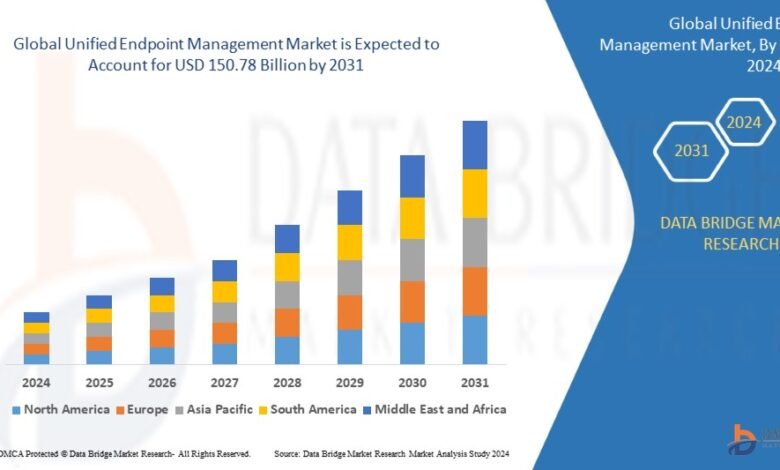
Growth Rate of Unified Endpoint Management Market
The size of the worldwide market for unified endpoint management was estimated at USD 9.85 billion in 2023 and is expected to grow at a compound annual growth rate (CAGR) of 40.65% from 2024 to 2031, reaching USD 150.78 billion.
Read More: https://www.databridgemarketresearch.com/reports/global-unified-endpoint-management-market
Conclusion
Unified Endpoint Management is a powerful tool for enhancing enterprise security in a world where the number and diversity of endpoints are rapidly increasing. By providing centralized control, real-time threat detection, and automation of security tasks, UEM helps enterprises stay ahead of evolving cyber threats. Moreover, it ensures that businesses can maintain compliance with regulatory requirements while protecting their sensitive data and assets from breaches and other security risks. As cyber threats continue to evolve, the adoption of UEM will become increasingly critical for businesses looking to secure their digital infrastructure and ensure the safety of their data.






